

{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"sagemaker:DescribeDomain",
"sagemaker:ListDomains",
"sagemaker:ListUserProfiles",
"sagemaker:ListApps"
],
"Resource": "*",
"Effect": "Allow",
"Sid": "AmazonSageMakerStudioReadOnly"
},
{
"Action": "sagemaker:AddTags",
"Resource": "*",
"Effect": "Allow",
"Sid": "AmazonSageMakerAddTags"
},
{
"Condition": {
"StringEquals": {
"sagemaker:ResourceTag/studiouserid": "${aws:PrincipalTag/studiouserid}"
}
},
"Action": [
"sagemaker:CreatePresignedDomainUrl",
"sagemaker:DescribeUserProfile"
],
"Resource": "*",
"Effect": "Allow",
"Sid": "AmazonSageMakerAllowedUserProfile"
},
{
"Condition": {
"StringNotEquals": {
"sagemaker:ResourceTag/studiouserid": "${aws:PrincipalTag/studiouserid}"
}
},
"Action": [
"sagemaker:CreatePresignedDomainUrl",
"sagemaker:DescribeUserProfile"
],
"Resource": "*",
"Effect": "Deny",
"Sid": "AmazonSageMakerDeniedUserProfiles"
},
{
"Action": [
"sagemaker:CreatePresignedNotebookInstanceUrl",
"sagemaker:*NotebookInstance",
"sagemaker:*NotebookInstanceLifecycleConfig",
"sagemaker:CreateUserProfile",
"sagemaker:DeleteDomain",
"sagemaker:DeleteUserProfile"
],
"Resource": "*",
"Effect": "Deny",
"Sid": "AmazonSageMakerDeniedServices"
}
]
}
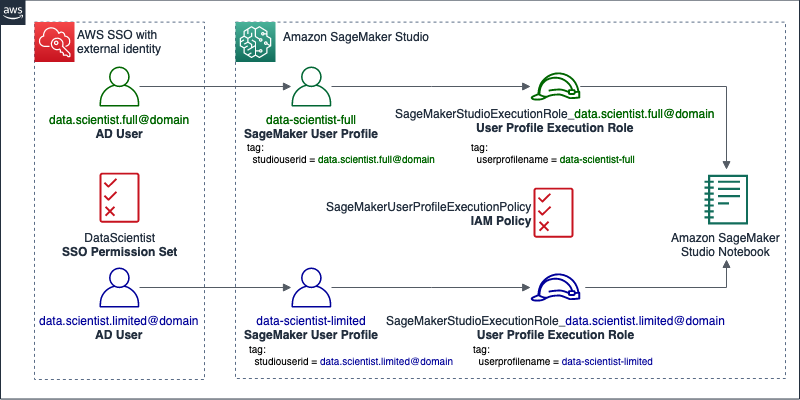
The policy allows users to access Studio, but only using a SageMaker user profile with a tag that matches their AD user name. It also denies the use of SageMaker notebook instances, allowing Studio notebooks only.
5. [Assign SSO access](https://docs.aws.amazon.com/singlesignon/latest/userguide/useraccess.html) into your AWS account to a group containing the data scientist users.
- In the **Select users or groups** page, type a group name containing the data scientist users in your connected directory.
- In the **Select permission sets** page, select the `DataScientist` permission set.
### Creating the required IAM group and users (only for authentication using AWS IAM):
To create your group and users, complete the following steps:
1. Sign in to the console using an IAM user with permissions to create groups, users, roles, and policies.
2. On the IAM console, [create policies on the JSON tab](https://docs.aws.amazon.com/IAM/latest/UserGuide/access_policies_create-console.html#access_policies_create-json-editor) to create a new IAM managed policy named `DataScientistGroupPolicy`.
- Use the following JSON policy document to provide permissions:
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"sagemaker:DescribeDomain",
"sagemaker:ListDomains",
"sagemaker:ListUserProfiles",
"sagemaker:ListApps"
],
"Resource": "*",
"Effect": "Allow",
"Sid": "AmazonSageMakerStudioReadOnly"
},
{
"Action": "sagemaker:AddTags",
"Resource": "*",
"Effect": "Allow",
"Sid": "AmazonSageMakerAddTags"
},
{
"Condition": {
"StringEquals": {
"sagemaker:ResourceTag/studiouserid": "${aws:username}"
}
},
"Action": [
"sagemaker:CreatePresignedDomainUrl",
"sagemaker:DescribeUserProfile"
],
"Resource": "*",
"Effect": "Allow",
"Sid": "AmazonSageMakerAllowedUserProfile"
},
{
"Condition": {
"StringNotEquals": {
"sagemaker:ResourceTag/studiouserid": "${aws:username}"
}
},
"Action": [
"sagemaker:CreatePresignedDomainUrl",
"sagemaker:DescribeUserProfile"
],
"Resource": "*",
"Effect": "Deny",
"Sid": "AmazonSageMakerDeniedUserProfiles"
},
{
"Action": [
"sagemaker:CreatePresignedNotebookInstanceUrl",
"sagemaker:*NotebookInstance",
"sagemaker:*NotebookInstanceLifecycleConfig",
"sagemaker:CreateUserProfile",
"sagemaker:DeleteDomain",
"sagemaker:DeleteUserProfile"
],
"Resource": "*",
"Effect": "Deny",
"Sid": "AmazonSageMakerDeniedServices"
}
]
}
The policy allows users in the group to access Studio, but only using a SageMaker user profile with a tag that matches their IAM user name. It also denies the use of SageMaker notebook instances, allowing Studio notebooks only.
1. [Create an IAM group](https://docs.aws.amazon.com/IAM/latest/UserGuide/id_groups_create.html).
- For **Group name**, enter `DataScientists`.
- Search and attach the AWS managed policy named `DataScientist` and the IAM policy created in the previous step.
2. [Create two IAM users](https://docs.aws.amazon.com/IAM/latest/UserGuide/id_users_create.html#id_users_create_console) named `data-scientist-full` and `data-scientist-limited`.
Alternatively, you can provide names of your choice, as long as they’re a combination of lowercase letters, numbers, and hyphen (-). Later, you also give these names to their corresponding SageMaker user profiles, which at the time of writing [only support those characters](https://docs.aws.amazon.com/sagemaker/latest/APIReference/API_CreateUserProfile.html#sagemaker-CreateUserProfile-request-UserProfileName).
### Creating the required IAM roles:
To create your roles, complete the following steps:
1. On the IAM console, [create a new managed policy](https://docs.aws.amazon.com/IAM/latest/UserGuide/access_policies_create-console.html#access_policies_create-json-editor) named `SageMakerUserProfileExecutionPolicy`.
- Use the following JSON policy document to provide permissions, providing your AWS Region and AWS account ID:
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"sagemaker:DescribeDomain",
"sagemaker:ListDomains",
"sagemaker:ListUserProfiles",
"sagemaker:ListApps"
],
"Resource": "*",
"Effect": "Allow",
"Sid": "AmazonSageMakerStudioReadOnly"
},
{
"Action": "sagemaker:AddTags",
"Resource": "*",
"Effect": "Allow",
"Sid": "AmazonSageMakerAddTags"
},
{
"Action": "sagemaker:DescribeUserProfile",
"Resource": "arn:aws:sagemaker:<aws region>:<account id>:user-profile/*/${aws:PrincipalTag/userprofilename}",
"Effect": "Allow",
"Sid": "AmazonSageMakerAllowedUserProfile"
},
{
"Action": "sagemaker:DescribeUserProfile",
"Effect": "Deny",
"NotResource": "arn:aws:sagemaker:<aws region>:<account id>:user-profile/*/${aws:PrincipalTag/userprofilename}",
"Sid": "AmazonSageMakerDeniedUserProfiles"
},
{
"Action": "sagemaker:*App",
"Resource": "arn:aws:sagemaker:<aws region>:<account id>:app/*/${aws:PrincipalTag/userprofilename}/*",
"Effect": "Allow",
"Sid": "AmazonSageMakerAllowedApp"
},
{
"Action": "sagemaker:*App",
"Effect": "Deny",
"NotResource": "arn:aws:sagemaker:<aws region>:<account id>:app/*/${aws:PrincipalTag/userprofilename}/*",
"Sid": "AmazonSageMakerDeniedApps"
},
{
"Action": [
"lakeformation:GetDataAccess",
"glue:GetTable",
"glue:GetTables",
"glue:SearchTables",
"glue:GetDatabase",
"glue:GetDatabases",
"glue:GetPartitions"
],
"Resource": "*",
"Effect": "Allow",
"Sid": "LakeFormationPermissions"
},
{
"Effect": "Allow",
"Action": [
"s3:CreateBucket",
"s3:GetObject",
"s3:PutObject"
],
"Resource": [
"arn:aws:s3:::sagemaker-audit-control-query-results-<aws region>-<account id>",
"arn:aws:s3:::sagemaker-audit-control-query-results-<aws region>-<account id>/*"
]
},
{
"Action": "iam:PassRole",
"Resource": "*",
"Effect": "Allow",
"Sid": "AmazonSageMakerStudioIAMPassRole"
},
{
"Action": "sts:AssumeRole",
"Resource": "*",
"Effect": "Deny",
"Sid": "DenyAssummingOtherIAMRoles"
}
]
}
This policy provides limited IAM permissions to Studio. For more information on recommended policies for team groups in Studio, see [Configuring Amazon SageMaker Studio for teams and groups with complete resource isolation](https://aws.amazon.com/blogs/machine-learning/configuring-amazon-sagemaker-studio-for-teams-and-groups-with-complete-resource-isolation/). The policy also provides common coarse-grained IAM permissions to the data lake, leaving Lake Formation permissions to control access to Data Catalog resources and Amazon S3 locations for individual users and roles. This is the recommended method for granting access to data in Lake Formation. For more information, see [Methods for Fine-Grained Access Control](https://docs.aws.amazon.com/lake-formation/latest/dg/access-control-fine-grained.html).
2. [Create an IAM role](https://docs.aws.amazon.com/glue/latest/dg/create-an-iam-role-sagemaker-notebook.html) for the first data scientist (`data-scientist-full`), which is used as the corresponding user profile’s execution role.
- On the **Attach permissions policy** page, the AWS managed policy `AmazonSageMakerFullAccess` is attached by default. You remove this policy later, to maintain minimum privilege.
- For **Tags**, add the key `userprofilename` and the value `data-scientist-full`.
- For **Role name**, use the naming convention introduced at the beginning of this section to name the role `SageMakerStudioExecutionRole_data-scientist-full`.
3. To add the remaining policies, on the **Roles** page, choose the role name you just created.
4. Under **Permissions**, remove the policy `AmazonSageMakerFullAccess`.
5. Choose **Attach policies**.
6. Search and select the `SageMakerUserProfileExecutionPolicy` and `AmazonAthenaFullAccess` policies
7. Choose **Attach policy**.
8. Repeat the previous steps to create an IAM role for the second data scientist (`data-scientist-limited`).
- For **Tags**, add the key `userprofilename` and the value `data-scientist-limited`.
- For **Role name**, use the naming convention, such as `SageMakerStudioExecutionRole_data-scientist-limited`.
## [Proceed to the next section](./03_Grant_Permissions_With_Lake_Formation.md) to grant data permissions with Lake Formation.