# App Mesh在EKS上的å¯è§‚测性: X-Ray
注æ„:在开始本部分之å‰ï¼Œè¯·ç¡®ä¿å·²å®Œæˆå¸¦æœ‰EKSçš„App Meshçš„[环境æ建](base.md)。 æ¢å¥è¯è¯´ï¼Œä»¥ä¸‹å‡è®¾å·²é…置了App Meshçš„EKS群集å¯ç”¨ï¼Œå¹¶ä¸”满足先决æ¡ä»¶ï¼ˆaws,kubectl,jqç‰ï¼‰ã€‚
首先,将IAMç–ç•¥`arn:aws-cn:iam::aws:policy/AWSXRayDaemonWriteAccess`é™„åŠ åˆ°æ‚¨çš„EKS集群的EC2 auto-scaling group组ä¸ã€‚
è¦åœ¨äºšé©¬é€Šäº‘科技ä¸å›½åŒºåŸŸè¦é€šè¿‡å‘½ä»¤è¡Œé™„åŠ IAMç–略,请使用:
```
$ INSTANCE_PROFILE_PREFIX=$(aws cloudformation describe-stacks | jq -r '.Stacks[].StackName' | grep eksctl-appmeshtest-nodegroup-ng)
$ INSTANCE_PROFILE_NAME=$(aws iam list-instance-profiles | jq -r '.InstanceProfiles[].InstanceProfileName' | grep $INSTANCE_PROFILE_PREFIX)
$ ROLE_NAME=$(aws iam get-instance-profile --instance-profile-name $INSTANCE_PROFILE_NAME | jq -r '.InstanceProfile.Roles[] | .RoleName')
$ aws iam attach-role-policy \
--role-name $ROLE_NAME \
--policy arn:aws-cn:iam::aws:policy/AWSXRayDaemonWriteAccess
```
如果是AWS其他区域:
```
$ INSTANCE_PROFILE_PREFIX=$(aws cloudformation describe-stacks | jq -r '.Stacks[].StackName' | grep eksctl-appmeshtest-nodegroup-ng)
$ INSTANCE_PROFILE_NAME=$(aws iam list-instance-profiles | jq -r '.InstanceProfiles[].InstanceProfileName' | grep $INSTANCE_PROFILE_PREFIX)
$ ROLE_NAME=$(aws iam get-instance-profile --instance-profile-name $INSTANCE_PROFILE_NAME | jq -r '.InstanceProfile.Roles[] | .RoleName')
$ aws iam attach-role-policy \
--role-name $ROLE_NAME \
--policy arn:aws:iam::aws:policy/AWSXRayDaemonWriteAccess
```
å¯ç”¨App Meshæ•°æ®å¹³é¢çš„X-Ray tracing
```sh
helm upgrade -i appmesh-controller eks/appmesh-controller \
--namespace appmesh-system \
--set region=$AWS_DEFAULT_REGION \
--set serviceAccount.create=false \
--set serviceAccount.name=appmesh-controller \
--set image.repository=961992271922.dkr.ecr.cn-northwest-1.amazonaws.com.cn/amazon/appmesh-controller \
--set init.image.repository=919830735681.dkr.ecr.cn-northwest-1.amazonaws.com.cn/aws-appmesh-proxy-route-manager \
--set init.iamge.tag=v4-prod \
--set sidecar.image.repository=919830735681.dkr.ecr.cn-northwest-1.amazonaws.com.cn/aws-appmesh-envoy \
--set sidecar.image.tag=v1.20.0.0-prod \
--set tracing.enabled=true \
--set tracing.provider=x-ray
```
X-Ray守护程åºç”±[App Mesh Controller](https://github.com/aws/aws-app-mesh-controller-for-k8s) 自动注入到您的应用容器ä¸ã€‚使用以下命令进行验è¯ï¼š
```
$ kubectl -n appmesh-demo \
get pods
NAME READY STATUS RESTARTS AGE
colorgateway-69cd4fc669-p6qhn 3/3 Running 0 11m
colorteller-845959f54-4cj5v 3/3 Running 0 11m
colorteller-black-6cc98458db-pqbv6 3/3 Running 0 11m
colorteller-blue-88bcffddb-6bmlt 3/3 Running 0 11m
colorteller-red-6f55b447db-2ht5k 3/3 Running 0 11m
```
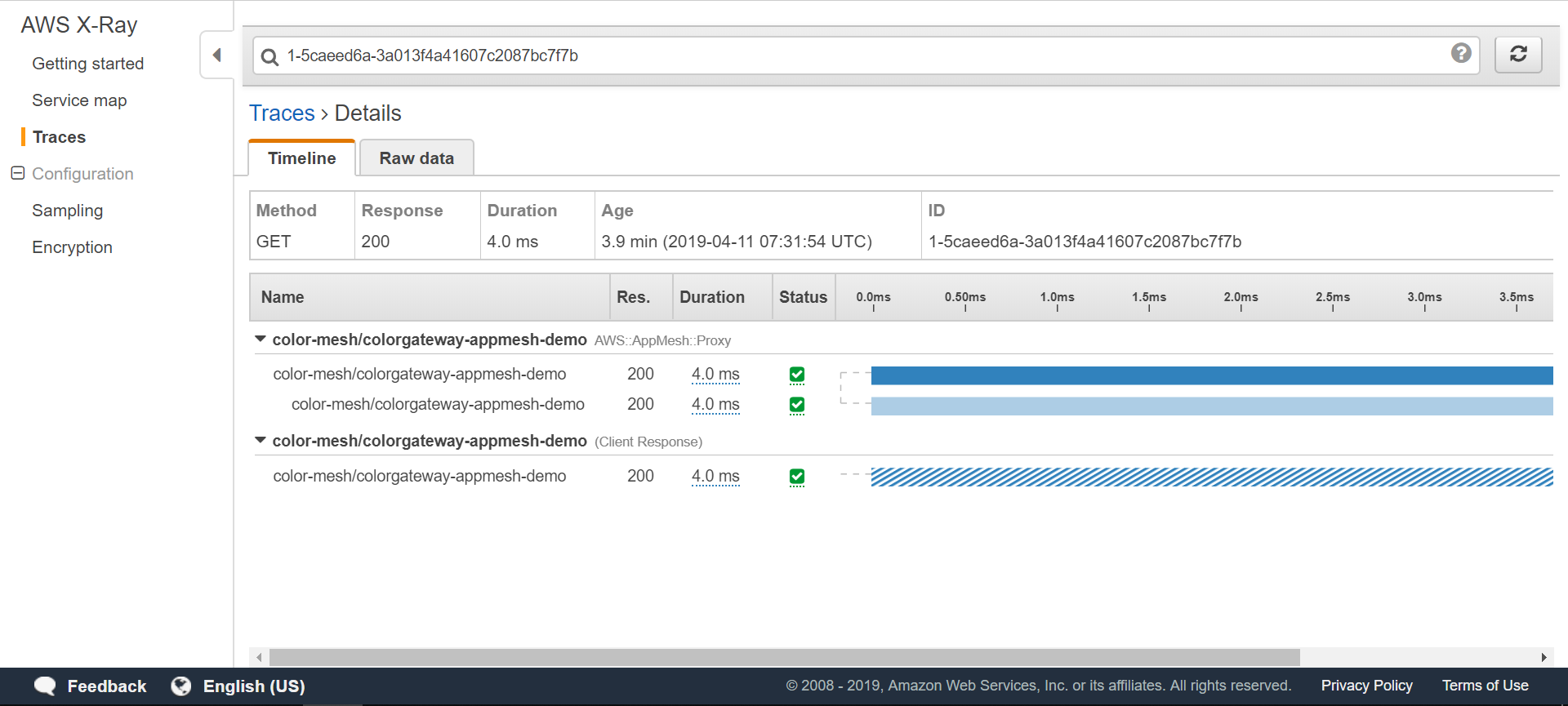
您在`READY` 列ä¸çœ‹åˆ°`3`了å—?这æ„味ç€æ¯ä¸ªåŠèˆ±ä¸è¿è¡Œç€ä¸‰ä¸ªå®¹å™¨ï¼šåº”用程åºå®¹å™¨æœ¬èº«ï¼Œä½œä¸ºApp Meshæ•°æ®å¹³é¢ä¸€éƒ¨åˆ†çš„Envoy,以åŠå°†è·Ÿè¸ªä¿¡æ¯æ供给X-RayæœåŠ¡çš„X-Ray代ç†ã€‚
我们现在å¯ä»¥çœ‹åˆ°æ•´ä¸ª[service map](https://docs.aws.amazon.com/xray/latest/devguide/xray-console.html#xray-console-servicemap)呈现了æœåŠ¡çš„调用线路:
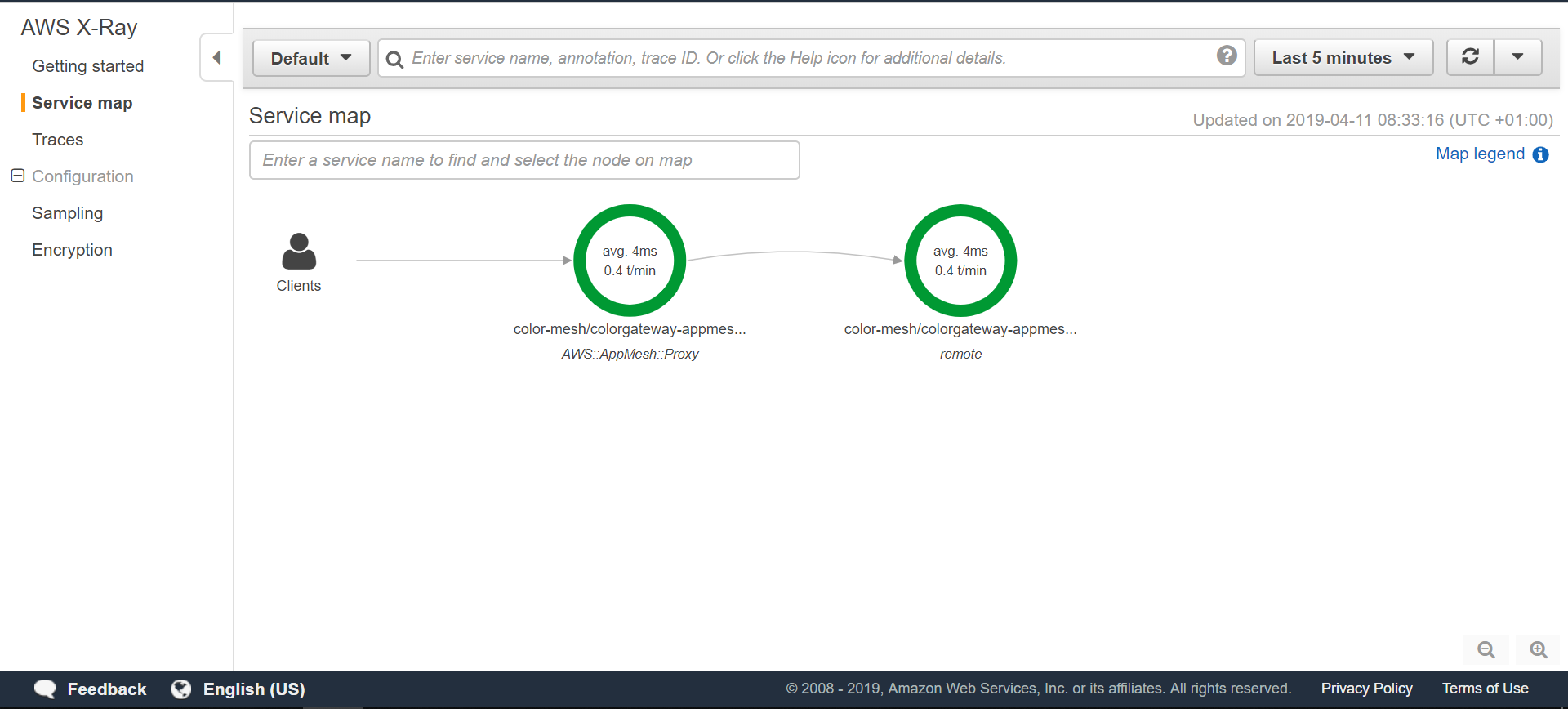
我们å¯ä»¥çœ‹åˆ°[跟踪](https://docs.aws.amazon.com/xray/latest/devguide/xray-concepts.html#xray-concepts-traces),这代表了沿ç€è¯·æ±‚路径的æœåŠ¡è°ƒç”¨ï¼š
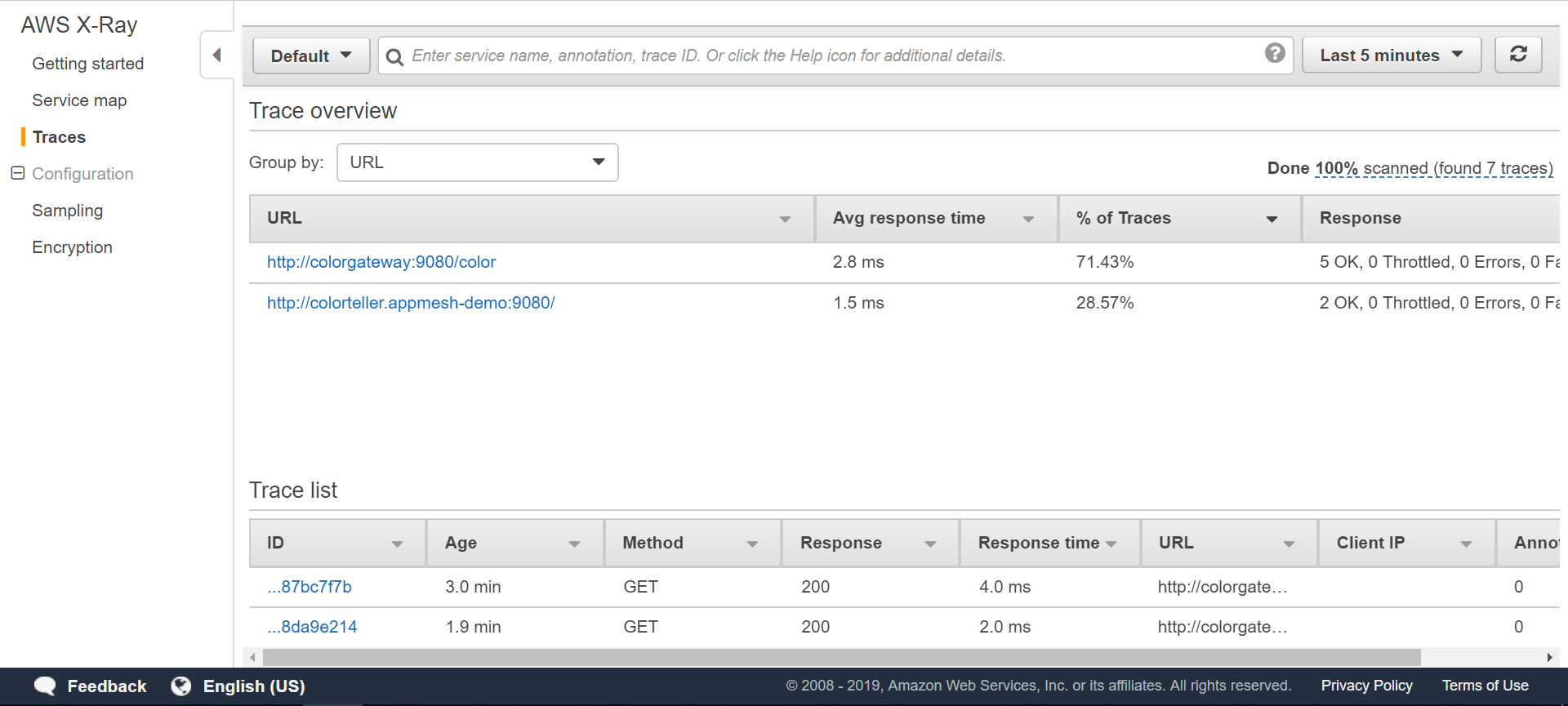
跟踪的详细视图: