**Step 1** : Open the AWS Console
1. Navigate to the Event Engine dashboard 2. Enter your **team hash** code. 3. Click **AWS Console**. The CloudFormation template for this round has already been prerun. ??? info "Click here if you're running this individually in your own AWS Account" Launch the CloudFormation stack below to setup the WildRydes application: Region| Deploy ------|----- US East 1 (N. Virginia) |  1. Click the **Deploy to AWS** button above (right click and open in a new tab). This will automatically take you to the console to run the template. 2. Click **Next** on the **Specify Template** section. 3. On the **Specify Details** step click **Next**. 4. Click **Next** on the **Options** section. 5. Finally, acknowledge that the template will create IAM roles under **Capabilities** and click **Create**. This will bring you back to the CloudFormation console. You can refresh the page to see the stack starting to create. Before moving on, make sure the stack is in a **CREATE_COMPLETE**. ## WildRydes identity overhaul You just joined a new DevOps team who manages a suite of animal-based ride sharing applications. Given your security background you've been embedded on the team to take the lead on security related tasks, evangelize security best practices, and represent your team when interacting with your security organization. Recently, your team inherited a new application; WildRydes. ## View your application 1. Open the Amazon CloudFormation console (us-east-1) 2. Click on the **Identity-RR-Wksp-Serverless-Round** stack or the **module-a7932bd25ca64049a57fd5bb055782db** stack (this is the stack name when created using Event Engine). 3. Click on **Outputs** and click on **WebsiteCloudFrontURL**. As part of the hand off to your team, the product team shared their vision for the application and stated that future iterations will include more dynamic features. After doing an evaluation of the architecture you determined that the WildRydes application is a static website hosted in an S3 bucket. There is a CloudFront Distribution setup to be used as a content delivery network and a Cognito User Pool for user management. ## Current application architecture 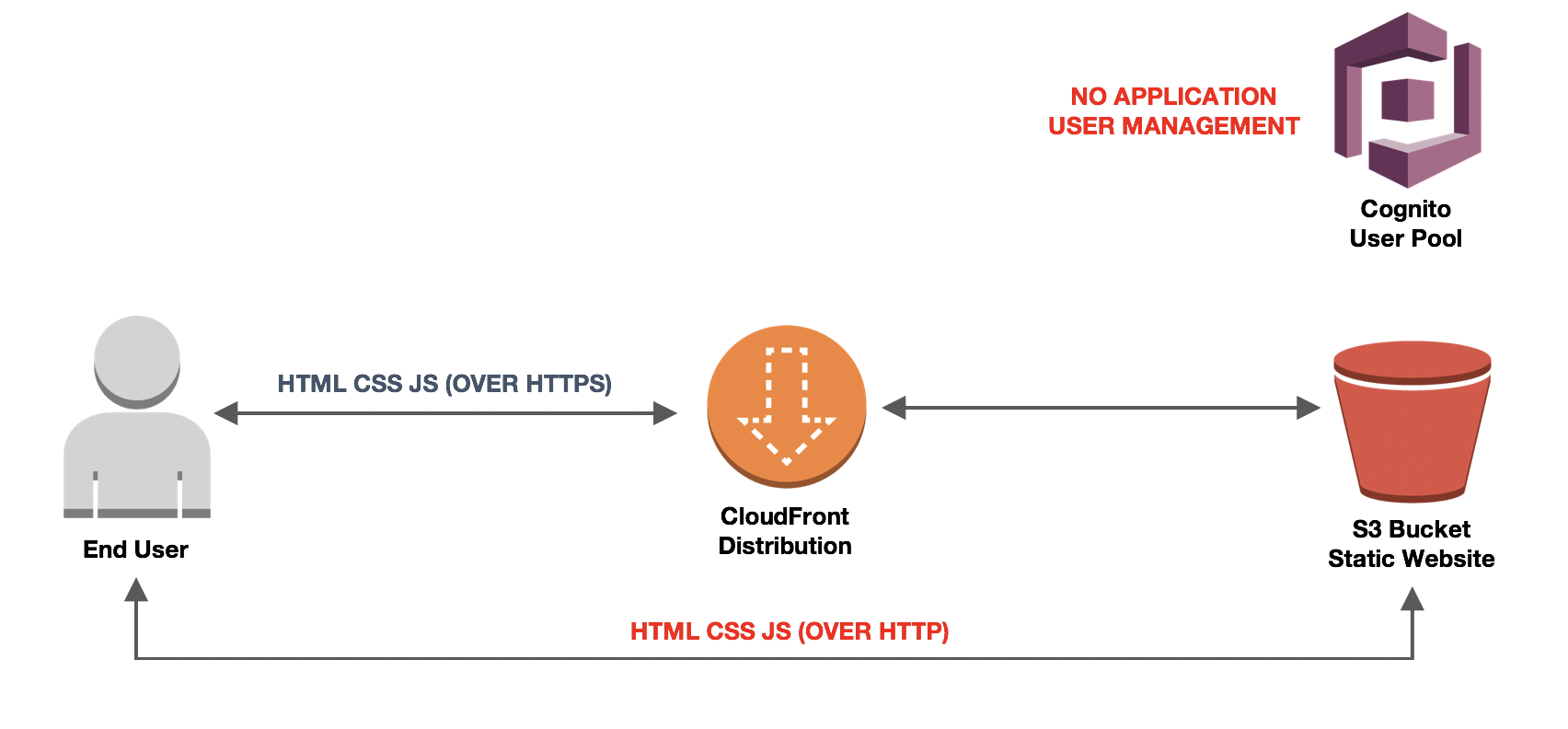 After thoroughly evaluating the architecture and doing a threat modeling exercise your team has identified a number of broken features and misconfigurations. It looks as though someone started putting in place certain security controls but were not able to fully implement them. These reviews resulted in the creation of a couple tasks that were added to the backlog for your team and given a high priority. *** Click Next to move on to **Task 1**!