You can use the checkov CLI without `--bc-api-key`, `--repo-id` and `--branch`, the results will still display locally, without uploading to the bridgecrew cloud, for testing or local-only scan results.
{{% /notice %}} The results will show all the failed checks and link to a guide explaining the cause and how to fix them. Note the output also includes the filename and snippet of code that is misconfigured: 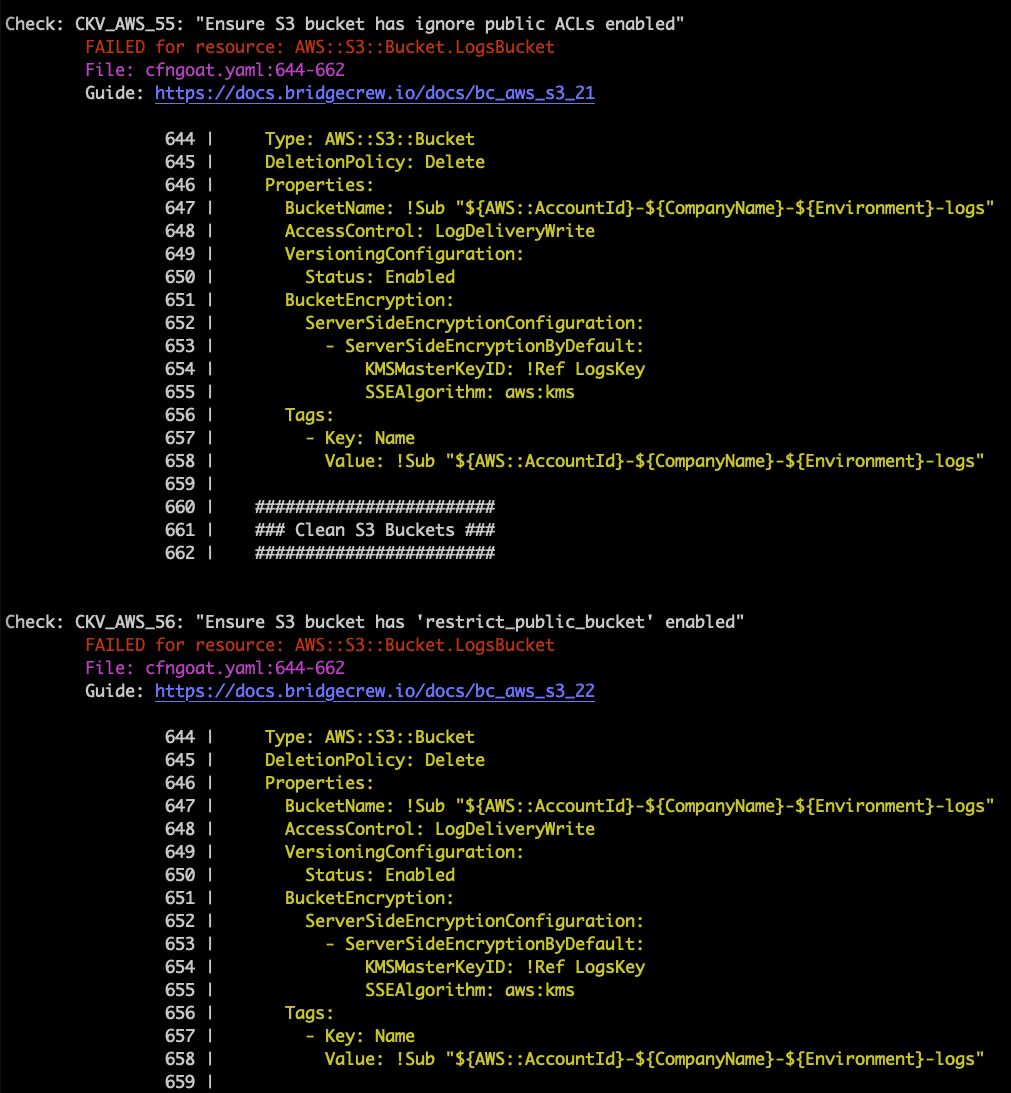 As you can see in the highlighted CLI output above, our demo CloudFormation repository has failing checks for two policies: - Ensure S3 bucket has ignore public ACLs enabled - Ensure S3 bucket ‘RestrictPublicBucket’ is set to True To get the list of policies builtin to your version of checkov, use -l or –list: ```bash checkov --list ``` ## Bridgecrew policies In many instances, when testing locally with the Checkov CLI, you may only be interested in running just a few checks. In that case, you can add the `-c` or `--check` option: ``` checkov -f cfngoat.yaml -c CKV_AWS_55,CKV_AWS_56 ``` Alternatively, if you want to run all but a few checks, use the `--skip-check` option: ``` checkov -f cfngoat.yaml --skip-check CKV_AWS_55,CKV_AWS_56 ``` Next, let’s inspect these results in the Bridgecrew dashboard.