# Palo Alto Networks VM-Series NGFW Module Example for AWS Cloud
A Terraform module example for deploying a VM-Series NGFW in AWS Cloud using the [User Data](https://docs.paloaltonetworks.com/vm-series/10-0/vm-series-deployment/bootstrap-the-vm-series-firewall/choose-a-bootstrap-method.html#idf6412176-e973-488e-9d7a-c568fe1e33a9_id3433e9c0-a589-40d5-b0bd-4bc42234aa0f) bootstrap method.
This example can be used to familarize oneself with both the VM-Series NGFW and Terraform - it creates two instances of virtualized firewalls in a Security VPC with three interfaces.
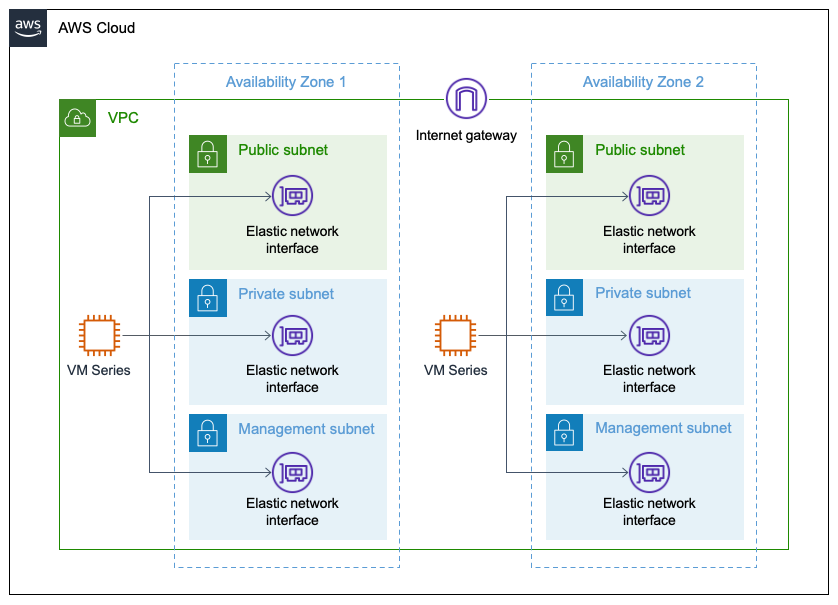
For a more complex scenario of using the `vmseries` module check the rest of our [Examples](https://github.com/PaloAltoNetworks/terraform-aws-vmseries-modules/tree/develop/examples).
**NOTE:**
The Security Group attached to the Management interface uses an inbound rule allowing traffic to port `22` and `443` from `0.0.0.0/0`, which means that SSH and HTTP access to the NFGW is possible from all over the Internet. You should update the Security Group rules and limit access to the Management interface, for example - to only the public IP address from which you will connect to VM-Series.
## Usage
Create a `terraform.tfvars` file and copy the content of `example.tfvars.sample` into it, adjust if needed.
Then execute:
```sh
terraform init
terraform apply
terraform output -json mgmt_eip
```
Connect through SSH to the VM-Series Management interface IP address using the SSH key you provided as the `ssh_key_name` parameter in your `terraform.tfvars` file:
```sh
ssh @ -i
```
## Cleanup
To delete all the resources created by the previous `apply` attempts, execute:
```sh
terraform destroy
```
## Requirements
| Name | Version |
|------|---------|
| [terraform](#requirement\_terraform) | >= 0.14.0 |
| [aws](#requirement\_aws) | ~> 3.74 |
## Providers
| Name | Version |
|------|---------|
| [aws](#provider\_aws) | ~> 3.74 |
## Modules
| Name | Source | Version |
|------|--------|---------|
| [security\_subnet\_sets](#module\_security\_subnet\_sets) | PaloAltoNetworks/vmseries-modules/aws//modules/subnet_set | n/a |
| [security\_vpc](#module\_security\_vpc) | PaloAltoNetworks/vmseries-modules/aws//modules/vpc | n/a |
| [security\_vpc\_routes](#module\_security\_vpc\_routes) | PaloAltoNetworks/vmseries-modules/aws//modules/vpc_route | n/a |
| [vmseries](#module\_vmseries) | ../../ | n/a |
## Resources
| Name | Type |
|------|------|
| [aws_kms_alias.vmseries](https://registry.terraform.io/providers/hashicorp/aws/latest/docs/resources/kms_alias) | resource |
| [aws_kms_key.vmseries](https://registry.terraform.io/providers/hashicorp/aws/latest/docs/resources/kms_key) | resource |
## Inputs
| Name | Description | Type | Default | Required |
|------|-------------|------|---------|:--------:|
| [bootstrap\_options](#input\_bootstrap\_options) | n/a | `any` | n/a | yes |
| [global\_tags](#input\_global\_tags) | n/a | `any` | n/a | yes |
| [name](#input\_name) | n/a | `any` | n/a | yes |
| [region](#input\_region) | n/a | `any` | n/a | yes |
| [security\_vpc\_cidr](#input\_security\_vpc\_cidr) | n/a | `any` | n/a | yes |
| [security\_vpc\_name](#input\_security\_vpc\_name) | n/a | `any` | n/a | yes |
| [security\_vpc\_routes\_outbound\_destin\_cidrs](#input\_security\_vpc\_routes\_outbound\_destin\_cidrs) | n/a | `any` | n/a | yes |
| [security\_vpc\_security\_groups](#input\_security\_vpc\_security\_groups) | n/a | `any` | n/a | yes |
| [security\_vpc\_subnets](#input\_security\_vpc\_subnets) | n/a | `any` | n/a | yes |
| [ssh\_key\_name](#input\_ssh\_key\_name) | n/a | `any` | n/a | yes |
| [vmseries](#input\_vmseries) | n/a | `any` | n/a | yes |
| [vmseries\_version](#input\_vmseries\_version) | n/a | `any` | n/a | yes |
## Outputs
| Name | Description |
|------|-------------|
| [public\_ips](#output\_public\_ips) | Map of public IPs created within the module. |

